Two-Factor Authentication
Since September 2023, Two-Factor Authentication (2FA) is required to login to terrabyte's login node and to login to the terrabyte portal. A second factor independent of your username and password was introduced to enhance the security of LRZ services. This is analogous to what you may be used to when authenticating to online banking and other sensitive web services.
You have the following options to set up your Two-Factor Authentication:
-
TOTP token: Your phone displays a new code every 30 seconds, which you have to enter as a second password following your normal username/password login. This is the recommended usage as it works with or without an active internet connection on your phone and no third-party servers are involved.
-
PUSH token: Your phone displays a login request that you have to confirm on your phone. While this might be more convenient, it has the caveat that messages have to be pushed via Apple/Google and this might result in delays or outages.
-
YubiKey: Alternatively, if you prefer authentification without a smart phone, you may use a YubiKey hardware key. See LRZ's Two-Factor Authentication via YubiKey documentation for instructions.
-
TAN-List: You may also use a printed TAN-List. See LRZ's Two-Factor Authentication via TAN-List for instructions.
You can also register all options in parallel. Anyway, we definitely recommend to roll out at least two redundant tokens, so that you have a backup-token if one or the other does not work. For each login, it is sufficient if one of several token checks succeeds. We recommend to have a TAN list at hand, which is independent from any technical device (e.g. if you brake, loose or switch your mobile phone).
Prerequisites
For 2FA login using PUSH or TOTP, we recommend the PrivacyIDEA app to be installed on your Android- or IOS-device .
You can install it via scanning the QR-code or manually by searching for privacyIDEA Authenticator (NetKnights GmbH) in your Play/App Store.

Activate 2FA
-
Go to https://simmfa.sim.lrz.de to generate your 2FA tokens and log in with your LRZ Credentials. If you just created a new account, please be aware that it may take some time until you can log in.
-
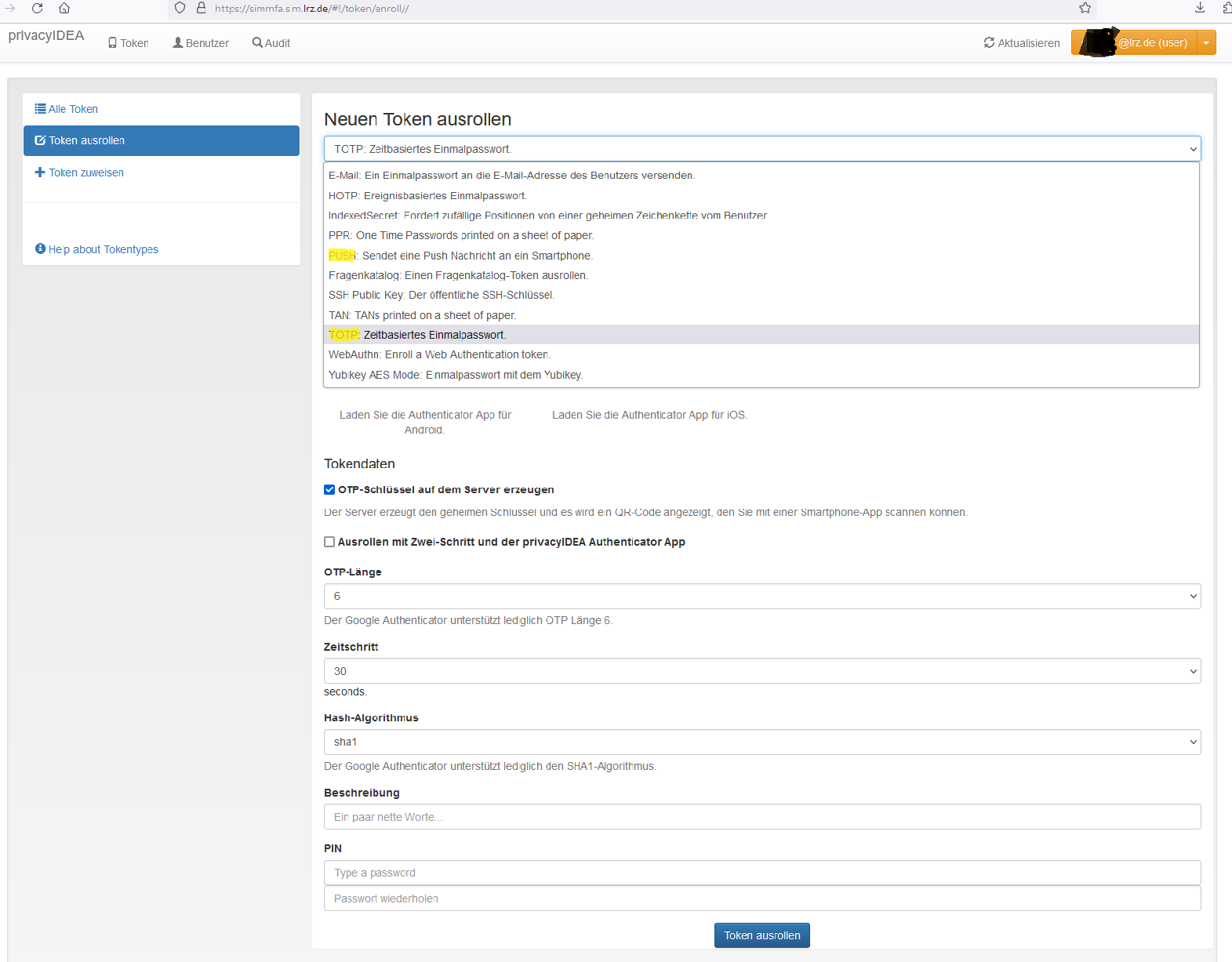
Choose "Token ausrollen" ("Enroll Token") from the menu on the left.
-
In the "Neuen Token ausrollen" ("Enroll new Token") window, choose TOTP, PUSH, TAN or Yubikey as type. Leave all other settings as they are (you may add a description to remember what device you registered the token on) and DO NOT define a PIN.
-
Then click on the "Token ausrollen" ("Enroll Token") button and scan the QR code with the privacyIDEA Authenticator app on your mobile phone, if displayed. If you rolled out a TAN list, print it out.
Do not delete the token if you have just one token activated! You will not be able to log into https://simmfa.sim.lrz.de anymore. This is another good reason to roll out multiple tokens using different methods (e.g. a TOTP token and a PUSH token).
Test 2FA
Website
You can test if your new token is working by logging into https://simmfa.sim.lrz.de again. After entering your LRZ-username and password, it should now also ask you for your token. For a TOTP token, type the code shown above your token into your privacyIDEA Authenticator app window. For a push token, confirm your login in the privacyIDEA Authenticator app below your token by clicking on "Akzeptieren" ("Accept").
SSH
You can test the 2FA login via SSH on the login node
login.terrabyte.lrz.de
.
You should first be asked for your username/password and then for your token. If
you choose a PUSH token leave the token field blank and just hit Enter.
If your work does not allow 2FA
There may be use cases for which 2FA is an obstacle. This mostly concerns fully automated workflows that rely on triggering jobs via SLURM without any manual inputs.
In most cases, such workflows (i.e. the software that manages such workflows) are lightweight enough to run as background process or cronjob on the login node. See job submission for more details. Since this doesn't involve SSH calls to SLURM, it also doesn't require 2FA for job submission (nevertheless, of course you need 2FA to set up the workflow management processes on the login node).
However, in some cases, users use workflow management software that is too resource demanding to permanently run on the login node or want to trigger SSH calls from an external system like e.g. a Kubernetes cluster or GitLab CI/CD. If this is your use case, please contact us via servicedesk@terrabyte.lrz.de so we can work on a customized solution together.